


Compliant E-Waste Disposal In The Education Industry
Education E-Waste Is A New and Increasing Issue. There is no denying that technology has become an enormous component of the education industry. From administration
Data sanitization refers to the deliberate process of permanently and irreversibly destroying data stored on memory devices. When done properly, data sanitization ensures that no data can be recovered, even with advanced data sanitization software. Data erasure, cryptographic erasure, and physical destruction are the three industry-wide methods of data sanitization.
Usually, when data is deleted using conventional methods like reformatting, the data is not really erased and can be recovered by someone with the requisite skills and software. This raises concerns about data privacy and security. On the other hand, proper data sanitization methods are deliberate and effective, ensuring permanent erasure.




The principal need for data sanitization is to protect sensitive personal and corporate data. The permanency and irreversibility of data sanitization methods ensure that when old electronic equipment is decommissioned or resold, all sensitive data is purged.
Stricter regulation around compliance has also necessitated the need for data sanitization. For instance, the EU’s General Data Protection Regulation (GDPR) demands that companies erase customer data upon request and prove subsequent data sanitization efforts.
Other industries and work contracts also have strict regulations that dictate the disposal of data. Fields like health care or government contractors must adhere to industry-specific guidelines for data disposal that requires the use of proper data sanitization methods.
Data sanitization is governed by various guidelines that are dictated by the type of industry, company, and needs a client may have. These guidelines are set to ensure data sanitization security.
Generally, the following data sanitization standards and policies apply:



While there is free data sanitization software in the market that promises to deliver complete data sanitization, there are 3 data sanitization techniques recognized as the most effective and best data sanitization methods. These are physical destruction, cryptographic erasure (or crypto erase), and data erasure. So let’s dive deeper below.
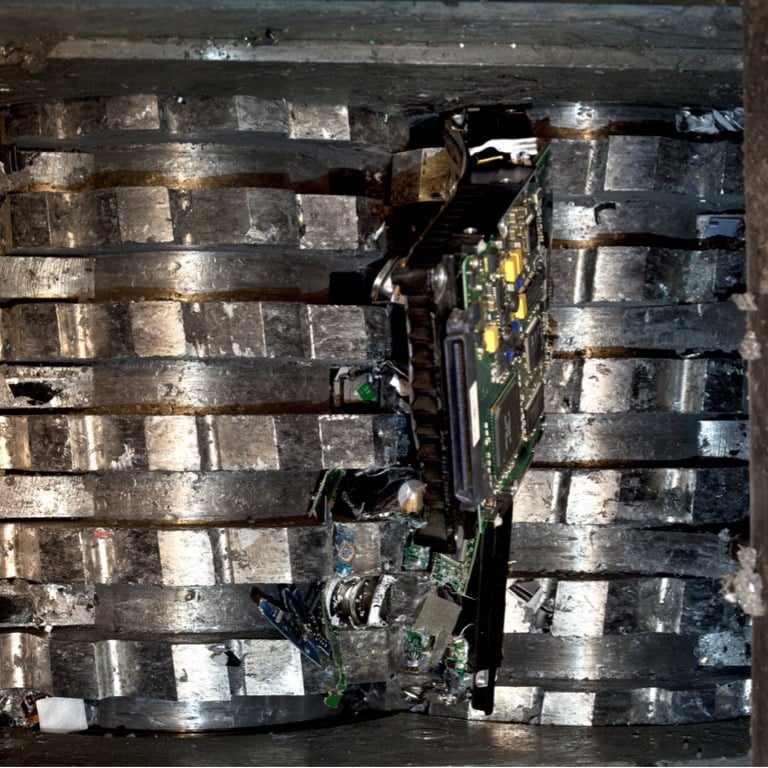
Physical destruction is the best data sanitization method. It refers to the process of physically shredding hard drives, smartphones, laptops, printers, and other storage devices into tiny pieces using large mechanical shredders or degaussers. Degaussing is a type of physical destruction method where data in decommissioned storage media is exposed to a powerful magnetic field. This neutralizes the data, making it unrecoverable. Degaussing is most effective on hard disk drives as well as tapes. However, these hard drives and tapes cannot be reused or resold. Degaussing is not regarded as an effective data sanitization tool for solid-state drives (SSDs).


This data sanitization method involves the use of encryption software to sanitize data. Cryptographic erasure works by using encryption software, whether built-in or manually deployed, on the entire set of data on the storage device, then deleting the key that would have been used to decrypt the data.
According to our partner Blancco, considered the gold standard in erasure software, the encryption algorithm must be a minimum of 128 bits and lists the following steps to ensure proper data sanitization through cryptographic erasure:
Data erasure, considered the highest form of securing data within data sanitization techniques, is software that writes over all the data with zeros and ones. This renders the data unrecoverable and achieves data sanitization on the storage device.
To achieve successful data erasure, Blancco notes that data erasure software must do the following:



When choosing an IT asset disposition (ITAD) partner, it is crucial to consider their data sanitization policy. Do they offer solutions that are tailor-made for your needs? What regulations do they abide by? What assurances do they offer? Are any reports and certificates verifiable and auditable? These are important considerations that an ITAD partner must satisfy beyond a shadow of a doubt before you can trust them with your business.
At TechReset, we are certified silver partners with Blancco, the world leader in erasure software, so you can be sure that our data sanitization techniques meet the highest and strictest demands in the market. Whatever your needs, we have partnered with the best-in-class and meet stringent worldwide standards for your benefit. Our data sanitization techniques are backed by a Certificate of Data Cleanse and an audit report that will detail the status of all your equipment. If you wish to resell your old equipment after the data sanitization process, we have partnered with Value Added Resellers to facilitate the best resale terms in Canada. We are a true ITAD partner in every sense of the word and are happy to partner with you throughout your data sanitization and asset disposition journey.



Education E-Waste Is A New and Increasing Issue. There is no denying that technology has become an enormous component of the education industry. From administration



TORONTO – TechReset was named one of Canada’s Top 100 Solution Providers during a special ceremony held on April 30, 2020. The annual ranking is



The question we often ask at TechReset is: How can we educate companies on the money they may be leaving on the table when they
A leader in the ITAD industry, TechReset goes beyond recycling computers. We fully repurpose units to extend the life of IT equipment beyond its first use. TechReset offers on-site device removal, certified audit reporting and completely secure data eradication through gold standard data cleanse software or physical hard drive shredding.
TechReset is a Division of OEM Corporation.
Head Office 2301 Royal Windsor Dr Unit #2 | Mississauga, ON | L5J 1K5, Canada








